Password managers for marketing teams
∙ 7 min ∙ Deutsch
If you use any digital devices, you really should be using a password manager. If you’re not, stop reading this post, go get yourself set up, and then come back.
In this post I’ll focus on lessons I’ve learned while working with a password managers in a work setting, specifically in marketing. The point of the exercise is to create a team-wide setup that secures your company’s online accounts to the highest degree possible while still enabling collaboration within the Marketing team.
I’m an avid 1Password user so you’ll likely feel that throughout this post. There may be other password managers that have an equally good mix of UX, features and security model. I just don’t happen to use those.
Understanding user models
There are several use cases you should have clear in your head when trying to understand if a password manager is right for your team, and when to use it.
Scenario 1: Each user has a set of login credentials and they can belong to an organization of users
This is the cleanest setup by the service and the one that doesn’t need a password manager for your team, making it possible for your team use a password manager to manage their private credentials wouldn’t hurt. The company account/page is a distinct concept to a user account. Users are contributors or admins on the company account, but their login credentials are theirs.
Examples: LinkedIn and Facebook company pages.
Note: Remind your team that it’s actually a bad idea for them to share their individual logins in a team setting in this case.
Scenario 2: Multiple users sharing a single account’s credentials
In this case, there is no distinction between the user and the company account. The company account is actually a single user account. You may be doing this because the platform doesn’t allow for anything else, or you may just not want multiple user accounts. This is where password managers shine.
Examples: Instagram and X company pages.
Let’s talk features
These are all important but in decreasing order of importance. I’m foregoing simple things like strong password generators (they should all support this) and cross-device support.
True multiuser setup
The password manager you choose should support true multiuser use. This seems a like a bit of no-brainer, but it’s not. A popular/free password manager, KeePass, doesn’t. In fact, they instruct you to share the database password with all those on your team to make multiuser possible. That’s insane to me, so I chose a password manager that allows individuals to have accounts and be part of a group.
Two-factor authentication
For the password manager itself: Look for a password manager that allows you to enforce two-factor authentication (2FA). If you’re going to centralize all your passwords, you should at least be paranoid about that repository getting compromised. I found that setting up the 2FA on several of my devices (both my smartphones and my tablet) means that I can almost always regain access if I need to.
For the saved websites/apps: This is something few password managers handle well but it’s critical! You should set up 2FA everywhere possible. This lets you have your cake and eat it too. You can enjoy great security on your accounts but still share the credentials with your team. This is much better than SMS-based 2FA in two ways. Firstly, from a security standpoint SMS-based 2FA is less secure due to SIM hacking. Secondly, it’s impractical in a team because only one phone will receive the one-time password.
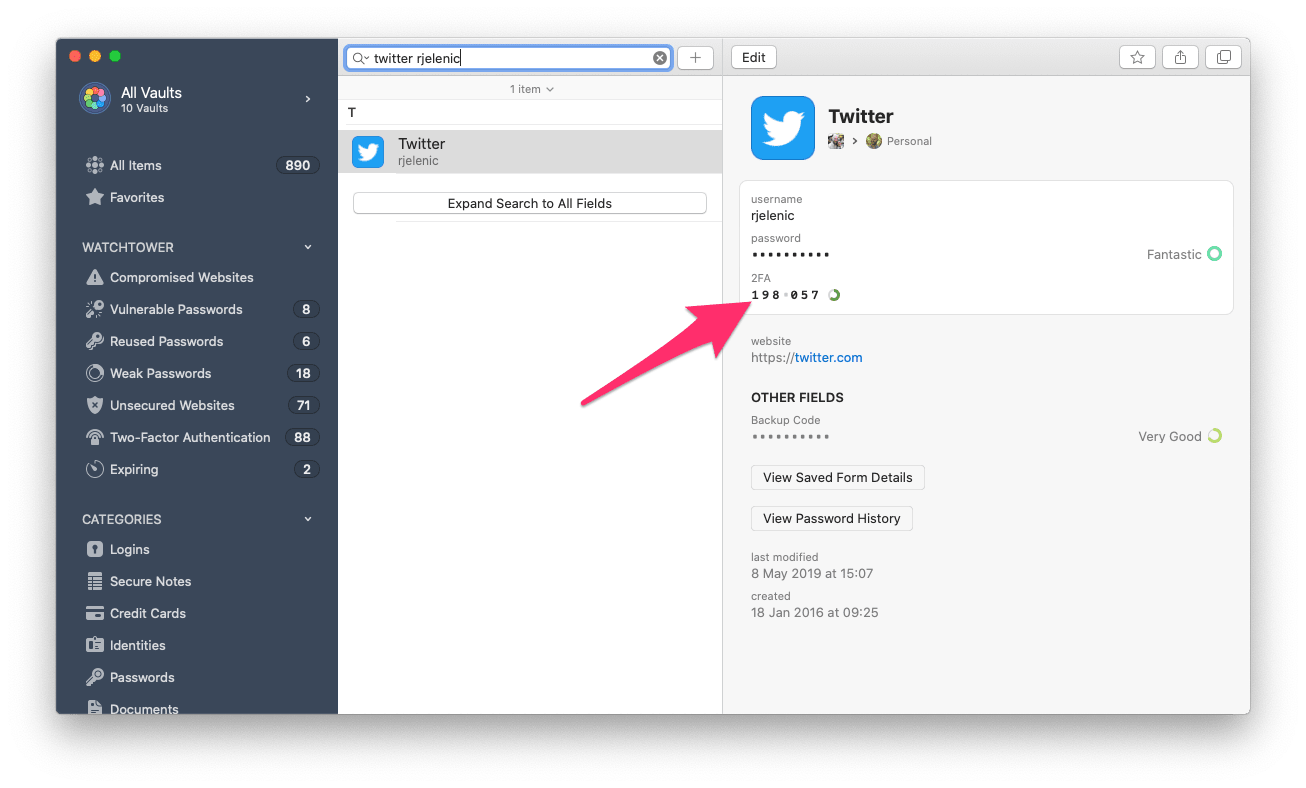
Some might argue that storing the 2FA one-time password in your password manager is bad form. I disagree. A good password manager will do a better job of alerting you to a new/suspicious login than most, if not all other services. The deterrent you put up by using 2FA on your accounts generally outweighs the danger of storing the 2FA inside the password manager itself, in my humble opinion. Remember, there’s no such thing as perfect security but making your accounts just a little harder to hack than the next person’s is enough to deter most hackers.
Granular access control
Not everyone in your team should have access to everything, so grouping logins together and controlling access is important. For example, only a few folks should have access to your company’s social media accounts. But everybody should have access to your stock image provider. You have to be able to distinguish these levels of access.
Different password managers will allow for different granularity of access control (usually increasing granularity comes with a higher price tag). But remember that a lot of granularity can also be a headache to manage. Strike the right balance here by trial-and-error.
Active directory
If your company has deployed some form of Active Directory, it might be worth coupling the password manager user access to that infrastructure. If someone leaves the company, the IT department revokes that employee’s access to everything (including your password manager) in a unified fashion.
Payment details
You may have connected a payment method to an account you’re sharing with your team. You’re making the decision that you trust those with access to not buy additional services without your consent. This is a judgement call you have to make…there’s no easy way to address this.
My recommendation: Have a clear talk with your team and let them know that they should be extra careful with those accounts. Anything that mentions “upgrade”, “bid”, “subscribe” or similar keywords that imply spend should raise red flags. Even unintentional misuse can have financial consequences for the company. This is a great time to make use of that access control.
Periodic session purging
A good habit to get into is purging all open sessions from team accounts with shared credentials periodically. This is a great time to change the password (in fact, you may need to change the password to purge the sessions, ironically). This logs all active users out and forces them to log back in. This will give you peace of mind that only those with access to that service in your password manager indeed get access. This is especially important if you modify access in the password manager. The service (eg. X) has no idea something happened in the password manager and it’s your job to reset all the sessions and force new logins.
When a team member leaves the company
People move on. It happens. A password manager lets you rapidly update your passwords on all the platforms that team member had access to via your password manager. Remember to not only change the password, but to also purge the sessions on the account (see above) if possible.
Sharing with users outside the password manager
Sometimes a single colleague in another department needs access to something you manage in your password manager. It’s possible you don’t want to add another user and pay the fees just to support that.
Some password managers, like 1Password, support guest users with limited access rights. Alternatively, share those passwords with those folks via an end-to-end encrypted channel like WhatsApp, iMessage, Signal or Telegram. Avoid email or enterprise chat services like Slack, Microsoft Teams or Skype, because those services aren’t end-to-end encrypted. Essentially, those companies could decrypt your messages and thereby gain knowledge of your account credentials, however unlikely that is.
A word on training
Most people don’t use a password manager. So make sure you take the time to get everyone up to speed on why you’re planning on using a password manager at work. If your team understands the logic and knows it’s coming well in advance, change becomes easier. This is something I don’t always do well, I must admit.
It helps to choose a password manager with a great support system. 1Password and LastPass both check this box, as I’m sure many others do.
